In the dynamic realm of technology, Android smartphones have become an integral part of our daily lives, serving as our go-to device for communication, entertainment, productivity, and much more. However, lurking beneath the surface of the Google Play Store are counterfeit apps disguised as legitimate system applications, ready to compromise your device’s security and privacy. In this comprehensive guide, we delve deep into the world of fake Android system apps, uncovering the telltale signs, potential risks, and effective prevention measures.
Understanding Fake Android System Apps
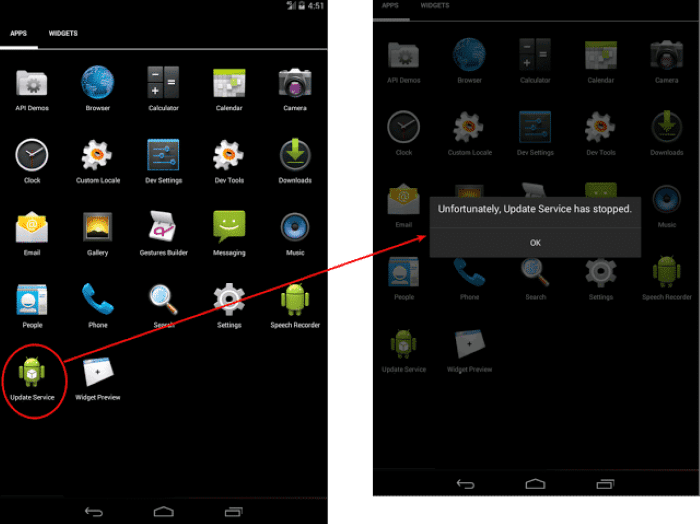
What are Fake Android System Apps?
- Definition: Fake Android system apps mimic genuine system applications, often masquerading as essential tools or utilities.
- Purpose: These malicious apps aim to deceive users into believing they are legitimate, gaining access to sensitive data or injecting malware onto the device.
- Common Examples: Fake system apps may impersonate system updates, security scanners, or device optimization tools.
How Do Fake Android System Apps Operate?
- Distribution Channels: Fraudulent apps primarily infiltrate devices through third-party app stores, malicious websites, or deceptive advertisements.
- Techniques: Developers employ various tactics such as social engineering, obfuscation, and cloaking to bypass security measures and evade detection.
Identifying Fake Android System Apps
Suspicious Permissions:
- Genuine system apps typically require minimal permissions to function effectively. Be wary of apps requesting excessive access to personal data or device features unrelated to their purported functionality.
- Examples: Fake system apps may request permissions to access contacts, messages, call logs, or device administration privileges without valid justification.
User Reviews and Ratings:
- Prioritize apps with positive reviews and high ratings from reputable sources. Conversely, exercise caution when encountering apps with limited or dubious feedback, especially if accompanied by numerous complaints regarding functionality or security issues.
- Tip: Look beyond the overall rating and analyze individual reviews for insights into user experiences and potential red flags.
Developer Credibility:
- Research the developer’s reputation and track record within the Android community. Established developers with a history of releasing reputable applications are more likely to prioritize user trust and security.
- Verify developer credentials, including contact information, website domain, and presence on official platforms such as GitHub or LinkedIn.
Official Sources and Certifications:
- Whenever possible, download apps exclusively from trusted sources such as the Google Play Store or official manufacturer repositories. These platforms employ rigorous vetting processes to ensure app integrity and security.
- Look for certifications or endorsements from reputable organizations, indicating compliance with industry standards and best practices.
App Behavior and Functionality:
- Exercise caution if an app exhibits unexpected behavior or functionality inconsistent with its advertised features. Pay attention to excessive battery consumption, intrusive advertisements, or sudden redirects to unfamiliar websites.
- Conduct thorough testing and scrutiny of app performance before granting extensive permissions or accessing sensitive data.
Potential Risks of Fake Android System Apps
Data Theft and Privacy Breaches:
- Fake system apps may harvest sensitive information such as login credentials, financial data, or personal photographs, posing a significant risk of identity theft or unauthorized access.
- Mitigation: Regularly review app permissions, restrict access to sensitive data, and utilize reputable security solutions to detect and prevent data breaches.
Malware and Security Exploits:
- Malicious actors frequently embed malware payloads within fake system apps, exploiting vulnerabilities to compromise device security and facilitate unauthorized access or control.
- Prevention: Implement robust security measures, including antivirus software, regular system updates, and cautious app installation practices to mitigate the risk of malware infections.
Financial Fraud and Scams:
- Fake system apps may engage in fraudulent activities such as phishing, SMS scams, or unauthorized financial transactions, deceiving users into divulging sensitive information or making illicit payments.
- Vigilance: Exercise skepticism when prompted to provide financial or personal details within apps, especially if the legitimacy of the request is questionable.
Preventive Measures and Best Practices
Source Verification:
- Prioritize apps from reputable sources such as the Google Play Store, official manufacturer websites, or trusted app repositories endorsed by cybersecurity experts.
- Enable security features such as Google Play Protect to automatically scan and verify apps for potential threats before installation.
Permission Management:
- Review and manage app permissions judiciously, granting access only to essential functions and data required for the app’s intended purpose.
- Regularly audit app permissions and revoke access from apps exhibiting suspicious behavior or unnecessary data collection practices.
Security Software:
- Install reputable antivirus or mobile security applications capable of detecting and removing malicious software, including fake system apps and other forms of malware.
- Keep security software updated to safeguard against emerging threats and vulnerabilities in the Android ecosystem.
User Education:
- Educate users on the risks associated with fake Android system apps and the importance of exercising caution when downloading and installing applications.
- Promote cybersecurity awareness through informative resources, tutorials, and interactive workshops to empower users in making informed decisions.
In the ever-evolving landscape of mobile technology, safeguarding against the proliferation of fake Android system apps is paramount to protecting user privacy, security, and digital assets. By adopting a proactive approach to app selection, vigilant scrutiny of permissions, and adherence to best practices in cybersecurity, users can fortify their devices against potential threats and enjoy a safer and more secure mobile experience. Together, let us navigate the digital landscape with confidence and resilience, ensuring that authenticity prevails over deception in the realm of Android applications.


